Top 10 Cybersecurity Best Practices for 2025

In today’s digital age, cyber threats have evolved, making cybersecurity essential for personal and professional life. The need for specific security measures, such as multi-factor authentication and regular software updates, is critical due to increasing threats like credential theft and automated attacks. This guide explores emerging digital threats, top cybersecurity practices, and free tools to ensure your online safety in 2025.
Outline:
- Common Online threats
- Importance of Cybersecurity in IT
- Emerging Shifts in Cybersecurity
- Building a secure IT structure Today
- Top 10 cyber security Best Practices
- Free Tools to secure your online presence
Common Online Threats
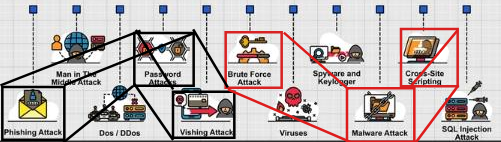
1. Insider Threats
Negligent or malicious insiders, including employees and contractors, can compromise digital assets like networks and data, leading to financial loss and reputational damage.
2. Social Engineering
Cybercriminals exploit human psychology to obtain sensitive data, using phishing emails, phone scams, and fraudulent text messages to acquire credit card details, usernames, and passwords.
3. Ransomware
Hackers encrypt files and demand payment, often in cryptocurrency, threatening data deletion, locking, or leakage to restore access.
4. Phishing
Attackers often employ deceptive emails or messages to scam victims into revealing sensitive credentials or downloading malware to spy on user activity
Importance of Cybersecurity
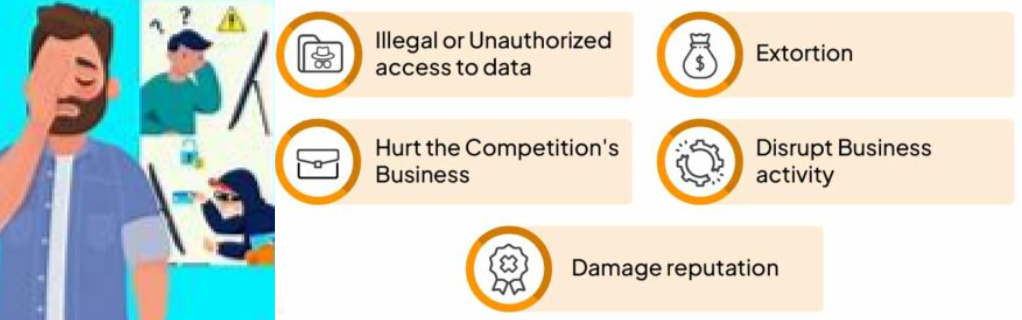
1. Enhancing Privacy
Cybersecurity secures digital assets by preventing unauthorized access and reducing exposure to identity theft.
2. Safeguarding Sensitive Data
Techniques like encryption, firewalls, and MFA help protect personal and corporate data from breaches
3. Preventing Emerging Threats
Regularly updating firewall rules and configurations, along with providing security awareness training, are essential to defend against evolving threats like zero-day exploits.
4. Compliance with Cyber Laws
Organizations must adhere to cybersecurity frameworks like GDPR, HIPAA, and ISO 27001 to enhance data protection.
Emerging Shifts in Cybersecurity
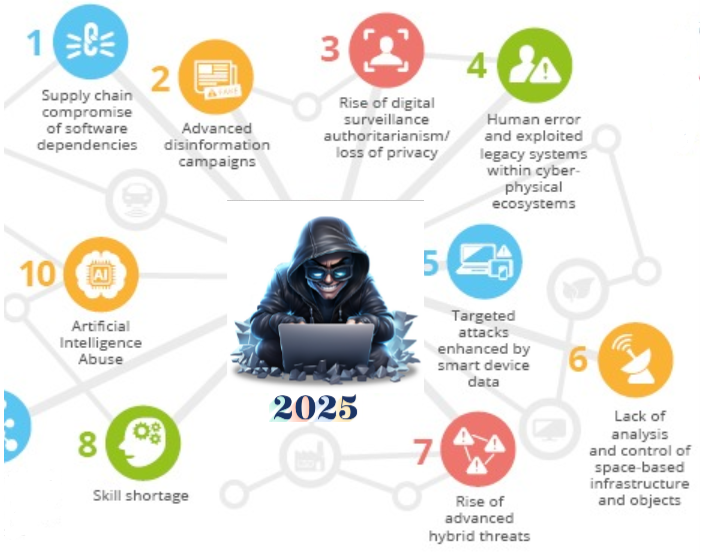
1. AI-Based Cyberattacks
AI enhances cybercriminal capabilities, enabling more sophisticated phishing, malware, and evasion techniques.
2. Quantum Computing Threats
Quantum computers could potentially break traditional encryption algorithms, exposing sensitive data to new risks.
3. Evolved Ransomware
Hackers use advanced techniques like fileless execution and AI-driven targeting to bypass detection and demand higher ransoms.
4. Deepfake Technology Abuse
AI-generated videos and audio clips are increasingly being used for identity theft, fraud, and misinformation campaigns.
Building a Secure IT Infrastructure
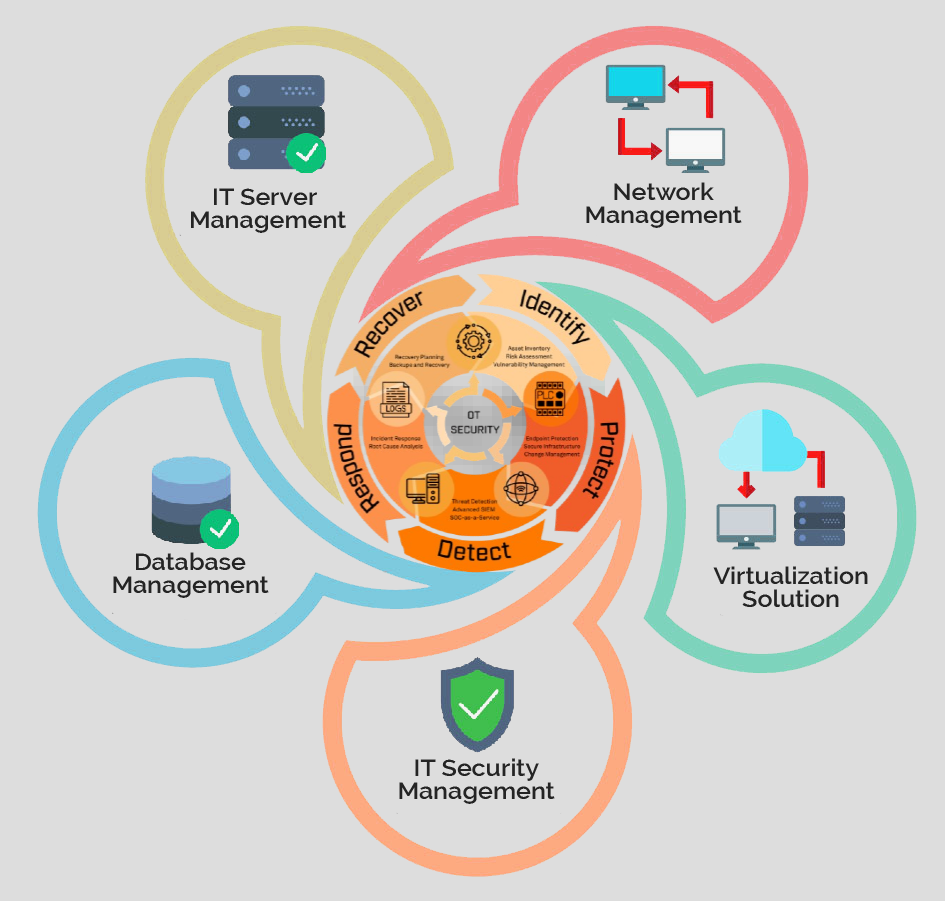
1. Risk Assessment & Identification
Organizations should conduct regular vulnerability analyses to prioritize risks and strengthen their cybersecurity defenses.
2. Strengthening Access Controls
Utilize role-based access control to prevent unauthorized access and enhance data security.
3. Data Encryption
Security teams should use strong encryption methods to ensure that sensitive data is protected from cyber threats.
4. Employee Training & Awareness
Educating employees about phishing, password security, and cyber threats reduces human involvement in cyber-crime.
Top 10 Cybersecurity Best Practices

1. Device Security
- Use multifactor authentication (e.g. biometric) and strong passwords.
- To stay ahead of attackers, automate software updates
- To prevent data loss, store data in encrypted cloud services.
2. Password Security
Combine Multi-Factor Authentication (MFA) and strong, unique passwords for different accounts.
3. Online Privacy
- Regularly review and update app permissions
- Use secure browsers and search engines to keep hackers at bay
4. Safe Internet Use
- Use VPNs and proxies to encrypt network traffic.
- Avoid clicking on suspicious links without proper verification
- Use safe (encrypted) and reputable messaging apps.
5. Social Media & Identity Protection
- Limit personal information sharing on social media
- Adjust privacy settings to restrict sensitive data visibility.
6. Secure Financial Transactions
- Enable online and offline real-time transaction alerts
- Avoid using ‘free’ public Wi-Fi for banking.
7. IoT Cybersecurity
- Change default usernames and passwords immediately
- Keep IoT devices on separate networks
- Regularly update firmware and software
8. Law Firm Cybersecurity
- Secure document management systems; encrypt client data
- Implement access control protocols
- Implement regulatory frameworks to ensure data protection
9. NSA Cybersecurity Practices
- Implement a zero-trust security model to prevent unauthorized access
- Use NSA-approved encryption measures
- Simulate phishing attacks to facilitate employee training and awareness
10. Cybersecurity for Employees
- Lock devices when not working (especially in between breaks).
- Use company-approved security software and hardware
- Secure home Wi-Fi with strong passwords to prevent unauthorized access
Free Tools to Secure Your Online Presence

1. Kaspersky Free Antivirus
- Provides real-time malware and virus protection.
- Allows automatic updates for emerging threats
👉 Download Here
2. Kaspersky Anti-Ransomware Tool
- Identifies and blocks ransomware attempts beforehand.
- Works in line with existing security software.
👉 Download Here
3. F-Secure Identity Theft Checker
- Scans potential data breaches involving personal information.
- Provides valuable security recommendations.
👉 Try It Here
4. F-Secure Strong Password Generator
- It Generates strong passwords.
- Helps users create unbreakable credentials.
👉 Use It Here
5. Proton VPN (Free Plan)
- Aids in encrypting internet traffic for private browsing.
- It has a’ No logs policy’ ensuring anonymity
👉 Sign Up Here
The digital world is constantly changing, and so are cyber threats. Enforcing strong cybersecurity practices, remaining informed about upcoming threats, and leveraging free security tools can significantly mitigate risks. Whether you are an individual or an organization, proactive measures will help defend your online presence in 2025 and beyond.
Stay secure, stay informed, and protect your digital world!

[…] It’s not all about security tools, it’s about awareness – create it by all means. Your cybersecurity tweets, videos, or posts might garner traction, and your platforms can qualify for monetization. Who knows, you might have just created an enviable career for yourself. […]